
Getting Started
LICENSING
LookInMyPC is licensed by computer. A license needs to be purchased that is commensurate with the number of computers it is installed on. Special pricing is available for multiple computer installations so please contact us if you need to install the program on more computers.
You can also run LookInMyPC from a USB thumb drive. In these cases, each thumb drive counts as one license, however there is no limit to the number of PC's you can use it with, as long as LookInMyPC is not permanently installed on them. Please refer to the section on portability below.
DESIGN
LookInMyPC was designed to take complicated things and make them easy. If you are a pro, you will understand it immediately. If you're not, LookInMyPC will bring a wide variety of information to you all in one place making a tough job much easier.
LookInMyPC was designed by computer professionals who troubleshoot PC's and networks all day. While many of it's features are available using other methods, they are cumbersome and take time and experience to navigate. Our goal here is to take a four hour job and turn it into a four minute job. Everything is "live" and fast with numerous drill-down and lookup options to help you keep your computer healthy with a minimum investment of time.
ORGANIZATION
LookInMyPC uses a non-standard directory structure by design. You may install LookInMyPC wherever you like, but the data it collects will always be stored in sub-directories under the installation directory. We purposely broke with the convention of storing data in the usual Program Data areas because we wanted to make LookInMyPC data easy to find for third party search and grep programs. Also, we designed the program to run "portable" from a USB thumb drive if desired. Keeping data storage consistent for various installations will help prevent issues in the future.
LookInMyPC does not use the system registry for any of its settings. Everything it needs is contained in the installation directory or one of it's sub-directories. If you run it from a USB thumb drive on multiple computers it will create a unique parent directory for each computer you use it on. Your settings can be different for each computer, and all logs and other data are kept separately. You don't have to do a thing, it takes care of everything for you.
PORTABILITY
Many users are responsible for the maintenance of two or more computers and might want to use LookInMyPC for spot-checking or occasional maintenance as issues arise. As mentioned above, LookInMyPC can be run from a USB thumb drive. To create a thumb drive installation, insert the thumb drive into your computer and run the setup program. Select the root folder of the thumb drive as the installation directory. That's all there is to it! Every computer you plug the thumb drive into will have it's own settings and log files automatically.
TERMINOLOGY
LookInMyPC uses professional terminology throughout the program and dialogs. Professional users will have no problems recognizing the terminology, but some less experienced users may need some clarification. Here are some of the most frequently asked questions:
What is a process?
A process is any application, program, or low-level system service that runs on your computer. These are also generically called "executables". Some of the processes running on your computer are visible, like word processors and browsers, but the vast majority of processes are not. They run in the background at various time throughout the day doing various things.
What does MD5 mean?
MD5 refers to a unique code that is generated from an actual executable file. We discuss this a little further down.
INSTALLATION
LookInMyPC is distributed as a normal Windows installation program. You just need to download and and run the installation program. The invoice you received on purchase contains a download button you can click to commence the download. We have a couple of recommendations for items you should do immediately after installing:
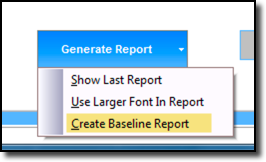
This will generate a baseline report of how your computer is configured today. A built-in function will allow you can compare future reports to this report and show you any changes. This is tremendously helpful in tracking down unexpected issues.
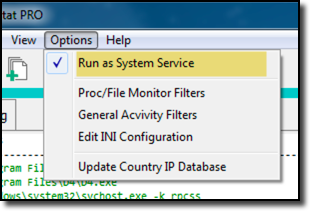
This installs and runs the service application and sets it to run on boot-up and log all activity no matter who is logged in, and even if no one is logged in at all.
The service adds several additional capabilities because it runs under the SYSTEM account, giving it access to activities that normal USER accounts would not have.
WITNESS OPERATION
Witness requires administrator permissions to run, so be sure you log in with an administrator account.
We should first stress that Witness is very safe. It is designed to monitor low level system activity, not intercept or change it. It is completely safe to explore its functions and reports. The only data the program writes is its own logs and settings.
There is only one caveat to this, and that is the ability to terminate and/or disable a process. This ability should be considered an emergency operation and used with care. If you disable a process and it turns out to be something you need, the operation can be reversed. So no permanent harm is done.
MAIN SCREEN
The main screen has two tabs open by default. The first tab, captioned Active Log, shows you what is going on in real time. Only current activity is shown. It is interesting to watch, especially on a busy computer. The second tab, captioned Todays Log, shows you the cumulative activity for the current day. As the day progresses, the log will get larger and you will be able to see things that occurred even if you weren't there to see them.
Please note that if you are running the standard version, your logs will only be maintained while the Witness user interface is open or minimized. If you exit the program, no activity will be recorded. If you are using the PRO version, then the system service keeps logging activity all the time, regardless of whether the user interface is open.
HYPERLINKS
Witness uses hyperlinks wherever it is useful. Anything in green on a screen or dialog can be clicked to find out more information. When you click on a hyperlinked item, the program will first look internally for information, and if none is found, it will launch a properly formatted web search to help you. You don't have to copy/paste or type a single word.
MD5 SIGNATURES
Witness watches every process (program) that runs on your computer while it is active. When it see's a process opening it quickly calculates the MD5 signature of the process and if it has not been seen before, it stores that information and logs a WARNING that a previously unknown process was observed. If has already been seen before, it will compare MD5 signatures to determine if the program has been changed or altered in any way. If it has, it will log a WARNING, otherwise, it will log that it was run. All warnings contain hyperlinks allowing quick investigation of the process file. MD5 signatures are also hyperlinked and will allow you to search the web for references to help you determine whether the program is legitimate or not.
Note: When a program or Windows is updated, you will undoubtedly see several warnings. This is normal, Witness is just letting you know the program has changed.
DAILY REPORTS
Daily Reports are available at any time during the day by clicking on the Daily Report tool bar button. The report will contain all warnings and a selection of "top 10" highlights for various activities. Witness can send you a daily report automatically. The email report is sent immediately after midnight if the computer is on, or as soon as it is turned on if it has been off. To activate the automatic daily report do the following:
USING SEND
On several screens you will see a SEND button. This allows you to send snippets or entire logs to someone else that you select. This works in two ways. If you have text highlighted on the screen, it will send the selected text in the body of the email. If no text it highlighted, it will send the entire screen or related log file as a ZIP file attachment. Some logs can get quite large and this greatly reduces the size of the message.
Note: The recipient of a SEND will receive plain text. It will not be hyperlinked or colorized as you see it on the Witness screen.
EXPLORE
Let Witness accumulate some data for a day or two, then explore it's functions. See what programs run and find out if they connect somewhere without your knowledge. After awhile, you will get a bigger picture of normal behavior for your computer and easily be able to spot things that are abnormal. If you are using the PRO version, be sure to check out the special Merged system report. The PRO version service also records file activity for selected directories and it makes for a very interesting report.